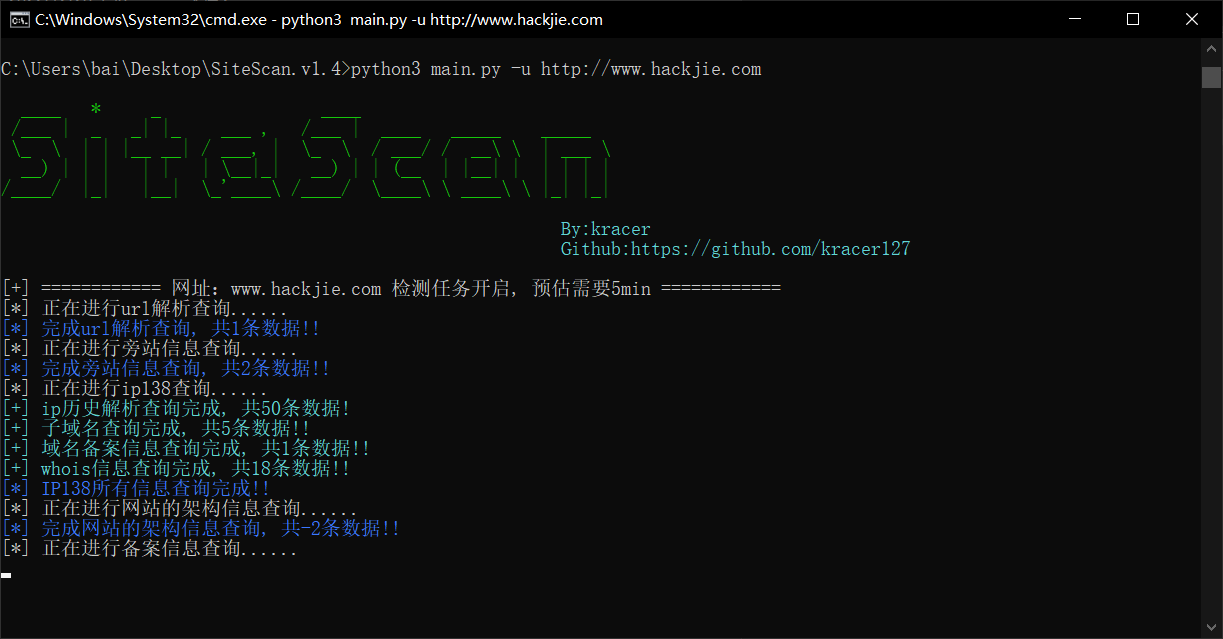
Dnsreaper介绍
dnsReaper是一款功能强大的子域名接管检测工具,该工具专为蓝队研究人员和漏洞猎人设计,并且能够在保证运行速度的情况下,提供较高的检测准确率。
DNS死神是另一个子域接管工具,但与强调准确性,速度和签名的数量在我们的武器库!
该工具每秒大约可以扫描50个子域名,并能针对每个子域名执行50次接管签名检测。这意味着大多数组织可以在不到10秒的时间内扫描整个DNS资产。
Dnsreaper 使用
要运行DNS Reaper,可以使用docker镜像或使用python 3.10运行它。
结果在输出中返回,更详细的信息在本地的“results.csv”文件中提供。作者还支持json输出作为选项。
使用Docker运行
docker run punksecurity/dnsreaper --help
使用Python运行
pip install -r requirements.txt python main.py --help
____ __ _____ _ __
/ __ \__ ______ / /__/ ___/___ _______ _______(_) /___ __
/ /_/ / / / / __ \/ //_/\__ \/ _ \/ ___/ / / / ___/ / __/ / / /
/ ____/ /_/ / / / / ,< ___/ / __/ /__/ /_/ / / / / /_/ /_/ /
/_/ \__,_/_/ /_/_/|_|/____/\___/\___/\__,_/_/ /_/\__/\__, /
PRESENTS /____/
DNS Reaper ☠️
Scan all your DNS records for subdomain takeovers!
usage:
main.py provider [options]
output:
findings output to screen and (by default) results.csv
help:
main.py --help
providers:
> aws - Scan multiple domains by fetching them from AWS Route53
> azure - Scan multiple domains by fetching them from Azure DNS services
> bind - Read domains from a dns BIND zone file, or path to multiple
> cloudflare - Scan multiple domains by fetching them from Cloudflare
> digitalocean - Scan multiple domains by fetching them from Digital Ocean
> file - Read domains from a file (or folder of files), one per line
> single - Scan a single domain by providing a domain on the commandline
> zonetransfer - Scan multiple domains by fetching records via DNS zone transfer
positional arguments:
{aws,azure,bind,cloudflare,digitalocean,file,single,zonetransfer}
options:
-h, --help Show this help message and exit
--out OUT Output file (default: results) - use 'stdout' to stream out
--out-format {csv,json}
--resolver RESOLVER Provide a custom DNS resolver (or multiple seperated by commas)
--parallelism PARALLELISM
Number of domains to test in parallel - too high and you may see odd DNS results (default: 30)
--disable-probable Do not check for probable conditions
--enable-unlikely Check for more conditions, but with a high false positive rate
--signature SIGNATURE
Only scan with this signature (multiple accepted)
--exclude-signature EXCLUDE_SIGNATURE
Do not scan with this signature (multiple accepted)
--pipeline Exit Non-Zero on detection (used to fail a pipeline)
-v, --verbose -v for verbose, -vv for extra verbose
--nocolour Turns off coloured text
aws:
Scan multiple domains by fetching them from AWS Route53
--aws-access-key-id AWS_ACCESS_KEY_ID
Optional
--aws-access-key-secret AWS_ACCESS_KEY_SECRET
Optional
azure:
Scan multiple domains by fetching them from Azure DNS services
--az-subscription-id AZ_SUBSCRIPTION_ID
Required
--az-tenant-id AZ_TENANT_ID
Required
--az-client-id AZ_CLIENT_ID
Required
--az-client-secret AZ_CLIENT_SECRET
Required
bind:
Read domains from a dns BIND zone file, or path to multiple
--bind-zone-file BIND_ZONE_FILE
Required
cloudflare:
Scan multiple domains by fetching them from Cloudflare
--cloudflare-token CLOUDFLARE_TOKEN
Required
digitalocean:
Scan multiple domains by fetching them from Digital Ocean
--do-api-key DO_API_KEY
Required
--do-domains DO_DOMAINS
Optional
file:
Read domains from a file (or folder of files), one per line
--filename FILENAME Required
single:
Scan a single domain by providing a domain on the commandline
--domain DOMAIN Required
zonetransfer:
Scan multiple domains by fetching records via DNS zone transfer
--zonetransfer-nameserver ZONETRANSFER_NAMESERVER
Required
--zonetransfer-domain ZONETRANSFER_DOMAIN
Required
运行机制
我们可以直接将目标域名列表以文件的形式提供给dnsReaper,也可以直接在命令行窗口中扫描单个域名。接下来,dnsReaper便会对目标域名进行扫描,并生成CSV结果文件。
除此之外,该工具还可以帮我们获取DNS记录,dnsReaper支持连接DNS服务提供商,并获取和测试目标域名的所有DNS记录。
当前版本的dnsReaper支持AWS Route53、Cloudflare和Azure,当然我们也可以自行添加其他的DNS服务商。
Dnsreaper工具下载
- 官方作者:https://github.com/punk-security/dnsReaper
- 小编提供百度云
Dnsreaper使用教程
安装pip相关包记得注意的点
1,版本号
2,运行报错问题
如:AttributeError: module ‘lib’ has no attribute ‘X509_V_FLAG_CB_ISSUER_CHECK’
扫描单域名
黑客街(hackjie.com)
- docker run punksecurity/dnsreaper single –domain hackjie.com
- python3 main.py single –domain hackjie.com
____ __ _____ _ __ / __ \__ ______ / /__/ ___/___ _______ _______(_) /___ __ / /_/ / / / / __ \/ //_/\__ \/ _ \/ ___/ / / / ___/ / __/ / / / / ____/ /_/ / / / / ,< ___/ / __/ /__/ /_/ / / / / /_/ /_/ / /_/ \__,_/_/ /_/_/|_|/____/\___/\___/\__,_/_/ /_/\__/\__, / PRESENTS /____/ DNS Reaper ☠️ Scan all your DNS records for subdomain takeovers! Domain 'hackjie.com' provided on commandline Testing with 61 signatures We found 0 takeovers ☠️ ⏱️ We completed in 1.62 seconds ...Thats all folks!
批量扫描
docker run -v $(pwd):/etc/dnsreaper punksecurity/dnsreaper file –filename 文件路径
python3 main.py file –filename 文件路径
1.本站上传的源码,均为平台购买,作者提供,网友推荐,互联网平台整理而来,请下载后24小时内删除。如有需要,请购买正版.
2.请勿利用文章内的相关技术从事非法测试,由于传播、利用此文所提供的信息而造成的任何直接或者间接的后果及损失,均由使用者本人负责,作者不为此承担任何责任。
3.站内资源若侵犯了您的合法权益,请指出本站立即改正。
4.上述内容仅供学习参考及技术交流之用,未经相关的知识产权权利人同意,用户不得进行商业使用。
5.保姆式服务,百分百售后!